Intro - In this tutorial we will learn How to use armitage for hacking windows XP as well as we will learn using of Meterpreter. I will Explain you simple and easiest way to run armitage in Kali Linux. I noticed one thing while starting armitage by going Application → kali linux → Exploitation Tools → Network Exploitation → armitage . There i got an error "Could not connect to database." If you are using first time Armitage on Kali linux then there are two way to run successfully armitage on your system. I will explain both separately.
A. How to open armitage.
1. Go to application → System Service → Metasploit → community/pro start
(click image for large view)
2. Type armitage and hit enter
1. Open terminal and type service postgresql start
2. again type in terminal service metasploit start
3. now type armitage
After one of above method follow these
4. after some time you will see this screen just click on connect
5. In next screen click on Yes
6. now armitage is connecting to database it takes little bit time
7. Your armitage has been successfully opened more explaination on image
8. Now be ready to start your work Here we are going Host →Nmap scan →Quick scan (OS Detect)
9. Here we need to write a range of victim IP address I am putting C grade range of IP so armitage will detect victim IP. This scan will be more easy if you know the victim IP address. There are many way to know the victim IP address we will discuss about it later.
10. Scan completed just click ok
11. Here we can see. Armitage found two victim. Here we will discuss about 192.168.75.131
Now we are going to Attacks → Find Attacks
12. Find attack scan completed click on ok
13. Now right click on victim pc go to Attack →smb → ms08_067_netapi
14. check “use a reverse connection” and click on launch
15. Here we can see 192.168.75.131 is rounded by red color. It means we have successfully caught Victim PC.
16. Now we are starting meterpreter. This is the 1st action which we can do with victim pc. Right click on victim 192.168.75.131 go to Meterpreter → Interact→ Command Shell
17. Here we are enter on Victim PC command. I will not explain more things about cmd as you know in cmd we can see all the directory and files, we can delete, remove, create files or folder , we can format drive etc…
18. 2nd action with Meterpreter. Goto Meterpreter → Explore → Browse Files
19. Here we are enter in victim explorer. We can upload a file or virus or backdoor. Use your mind and do whatever you want to do with your victim…
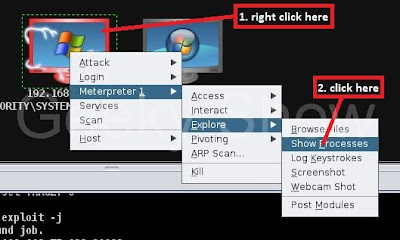
20. 3rd action with Meterpreter. Go to Meterpreter → Explore → Screenshot
21. when you click on screenshot (above image). You will see a screenshot of your victim pc. Through this you can get lot of information like what your victim is doing right now on his PC etc..
22. 4th action with Meterpreter. Go to Meterpreter → Explore → Log Keystrokes
23. click on launch
24. This is my Windows XP PC which I am using as victim PC. Here I am typing “I am victim” to show you how Log keystrokes work .
25. Here you can see here I got keystroke of my victim pc that is “I am victim”
26. 5th action with meterpreter. Go to Meterpreter →Explore → Show Processes
27. This is victim pc. he has opened notepad.
28. Here we are killing victim notepad. First of all select notepad extention then click on kill. By using this you can kill all programs which are running on victim pc etc…
(click image for large view)
if you like my tutorials please comment
Like it ? Share it.



































![SQL Injection Basics - Union Based [Detailed Tutorial]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjjQpa2wuMB-m5CXPVf71GUOkfiIOQA8KTyQ-_zfAl0SZa23UBN1QJaO2ZMGRDZlmDJTYf2jJ4ik3Xnj1locc38Yv9l6VMxTWt32s86JtXtLABDn20DRuAcbLPKMb9m2hc6PDmjIjvU-us/s72-c/SQL-Injection-Attack.jpg)



No comments:
Post a Comment